Id Mapping – You’ll then need to authenticate your identity to open that folder and access the app. You can’t lock or hide every app. For example, you can’t lock the Camera, Clock, or Watch apps, Apple Maps, or . It also analyzed the prevalence of identity theft and other forms of fraud, which are significant risks in the online dating world. More From Newsweek Vault: Online Banks vs. Traditional Banks: Learn .
Id Mapping
Source : segment.com
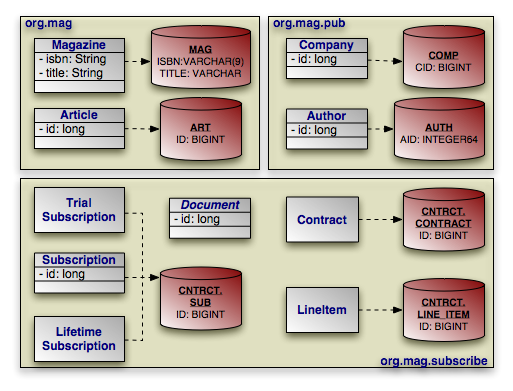
Customizing ID Mapping Framework (SAP Library SAP Solution Manager)
Source : help.sap.com
12.4. Identity Mapping
Source : docs.oracle.com
Customizing ID Mapping Framework (SAP Library SAP Solution Manager)
Source : help.sap.com
ID Mapping in CPI A Better Chance to Avoid Dupli SAP Community
Source : community.sap.com
User Identity Mapping In a Hybrid Environment, Part 2: ID Mapping
Source : www.egnyte.com
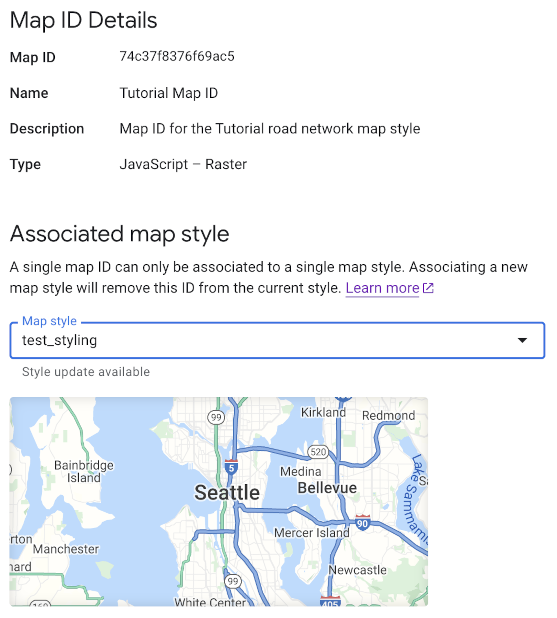
Google Maps Platform | Google for Developers
Source : developers.google.com
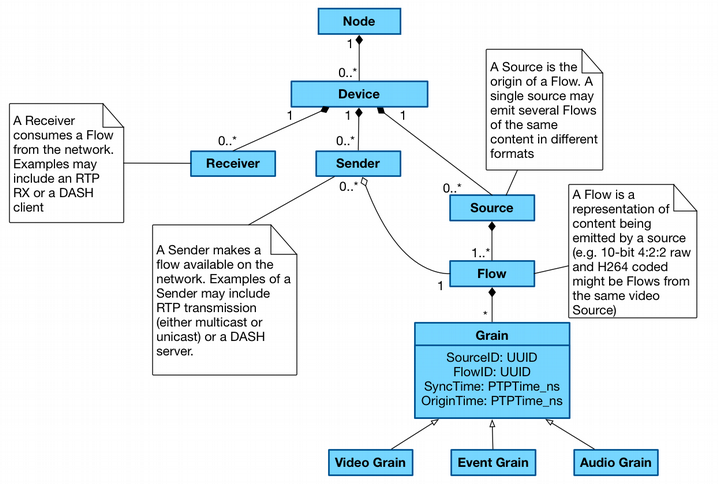
Data Model: Identifier Mapping | is 04
Source : specs.amwa.tv
Google Maps Platform | Google for Developers
Source : developers.google.com
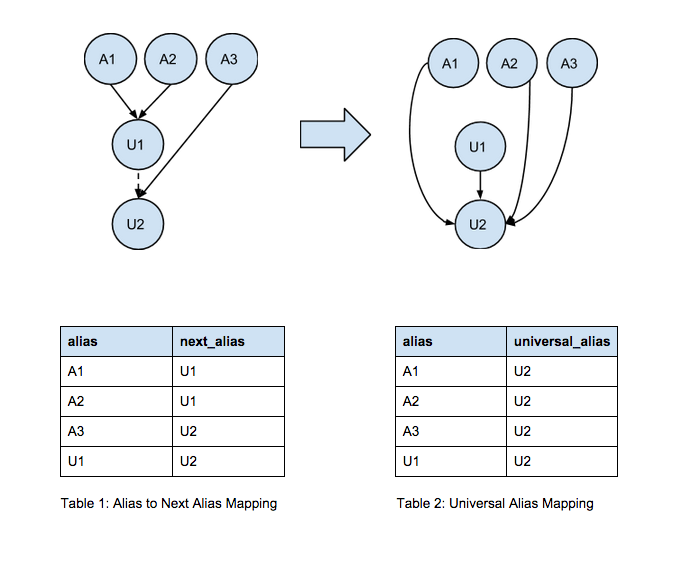
A Guide to Universal User ID Mapping | Twilio Segment
Source : segment.com
Id Mapping A Guide to Universal User ID Mapping | Twilio Segment: The superyacht capsized and sank after being struck by an over-sea tornado known as a waterspout off Sicily at around 3am GMT on Monday. . Federal hotspot mapping showed the fire on both sides of the highway for Custer County nonprofit animal shelter Heart of Idaho Animal Sanctuary was offering Stanley evacuees a safe place to .